Hey everyone! Today, I’m going to share a real-world case study on how I handled and removed malware from one of my client’s websites. If you’re currently facing similar issues or want to learn more about website security, this article is exactly what you’ve been looking for.
Table Of Content
- 1. Identifying the Attack Type: Signs of a Malware-Infected Website
- 2. Cleaning Malware-Containing Files: Rooting Out the Infection
- 3. Enabling IP Blocking: Preventing Botnets and Vulnerability Scans
- 4. De-indexing Malicious Redirect Links: Cleaning Google’s Reputation
- 5. Resubmitting Sitemap for Re-indexing: Providing a Clean Version to Google
- Conclusion: Real-World Experience in Website Malware Removal
1. Identifying the Attack Type: Signs of a Malware-Infected Website
Upon receiving the website from another developer, I immediately noticed it was heavily infected with malware. This particular client’s website was used for running advertisements (ads), which made it a prime target for botnet attacks and vulnerability scans.
Even though the ad campaigns had stopped, the website’s bandwidth was still being consumed at an extremely high rate, despite having very low traffic. This was a clear anomaly.
I checked the traffic and narrowed down the scope to determine if the website was under a DDoS attack. The result: it wasn’t a DDoS. DDoS attacks typically involve millions of requests at once, whereas here there were only tens of thousands.
The website was locked due to exceeding its monthly bandwidth limit. I helped the client migrate to another hosting provider with unlimited bandwidth. However, even after the migration, the bandwidth consumption remained alarmingly high.
My professional intuition told me the website might be infected with malware. When I started my checks, I wasn’t surprised – right from the first type of malware scan, I discovered the website was compromised with spamdex malware.
Spamdex is a sophisticated type of malware that allows hackers to create hidden files within the website’s source code. From these hidden files, they generate a multitude of “fake” links from the victim’s site, redirecting users to the hacker’s own site. Fortunately, the website had not yet been fully compromised with administrative control. (If you want to see a case study on handling full administrative compromise, click on this article here.)
2. Cleaning Malware-Containing Files: Rooting Out the Infection
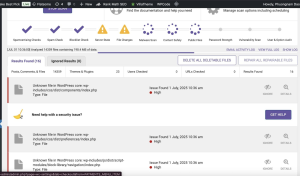
To remove this malware, I used the Wordfence Premium plugin to perform an initial scan of the entire website. The scan results revealed numerous suspicious files, likely containing malicious code.
I proceeded to delete all those files and then ran multiple re-scans to ensure that the cleanup process was thorough and no harmful files remained in the client’s source code. This is a crucial step for completely cleaning a website.
3. Enabling IP Blocking: Preventing Botnets and Vulnerability Scans
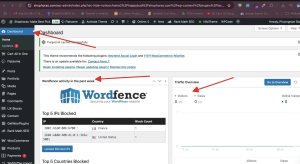
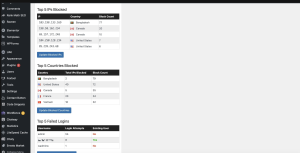
After cleaning up the malware, I enabled Wordfence’s IP Blocking feature. Immediately, I noticed several unusual IPs from Bangladesh, the US, and other countries. Notably, these were all IPs from rented VPS services like OVH, Vultr, etc. – indicating that the hackers were using these VPSs to launch botnet attacks.
Upon closer inspection, I confirmed that Wordfence wasn’t blocking legitimate traffic mistakenly. The plugin only blocked IPs exhibiting abnormal behavior, for instance:
- Regular users typically access URLs like:
yourdomain.com/category/post-1. - But bots would try to access sensitive files like:
yourdomain.com/wp-content/wrc.phporwp-config.php– which is clearly a vulnerability scan attempt.
Additionally, Wordfence automatically blocks IPs attempting to brute-force the admin password. For example, if an IP enters the wrong password 5 consecutive times, it will be immediately blocked. This feature significantly enhances WordPress website security.
4. De-indexing Malicious Redirect Links: Cleaning Google’s Reputation
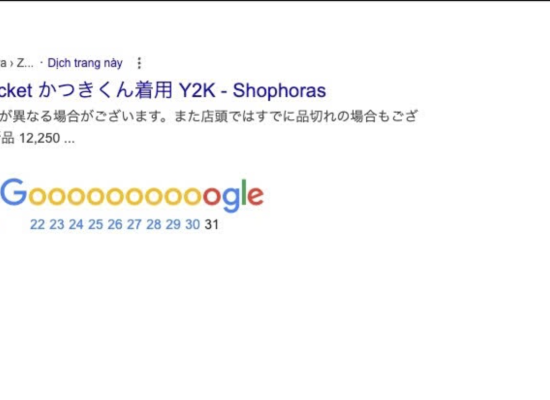
The client’s website was heavily affected by redirects: 35 pages and nearly 200 links had been created by the hacker. Since the client only focused on running ads and wasn’t performing SEO for these specific pages, removing these malicious links did not impact their existing SEO rankings.
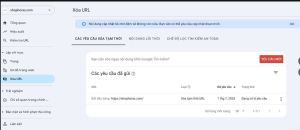
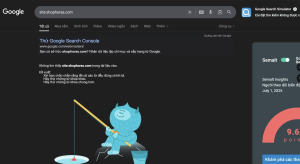
I used Google Search Console to submit a command for bulk removal of the malicious links from Google’s index. After approximately 4 hours, all the malicious links were completely removed from Google’s search results. This is a necessary step to mitigate the damage from spamdex malware.
5. Resubmitting Sitemap for Re-indexing: Providing a Clean Version to Google
After thoroughly cleaning all the malicious redirect links, I proceeded to resubmit the sitemap to Google. The purpose of this was to allow Google to re-index the entire website with its completely cleaned version for the client. This helps Google understand that your website is “clean” again and removes any lingering bad traces from the malware.
Conclusion: Real-World Experience in Website Malware Removal
I hope these practical experiences from this case study will help you address any malware issues your website might be facing. I believe this is precisely why you found and read this article.
If you’re still struggling with the process, don’t hesitate to message me. I specialize in providing support for malware removal and website security enhancement for businesses, as this is part of the services I offer.
Thank you for reading, and I look forward to seeing you in future articles with more valuable insights on SEO and website security!


No Comment! Be the first one.